About
Why
We want to be able to trust the Internet of Things. This is why we, as engineers, are working to make it more secure – even on inexpensive hardware.
How
We believe that low-cost hardware need not mean low security. So we leverage our engineering skills to create lightweight cryptographic code for massive IoT applications based on inexpensive microcontrollers.
What
We have created innovative solutions, platforms, and software components in the industrial, medical and consumer IoT, see our references. Since 2019, we focus on our crypto libraries. We work with device manufacturers, chip vendors, and IP vendors to create strong cryptography solutions for resource-constrained microcontrollers.
Who
We are a spinoff of the Swiss Federal Institute of Technology (ETH Zürich). Our innovation history and experience, in what today is called the Internet of Things, goes back 30 years.


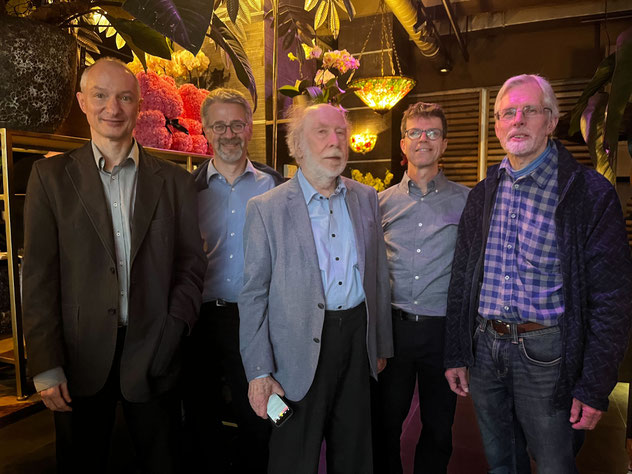
From our 30 years anniversary in 2023: management team and board of directors, with Prof. Niklaus Wirth as honorary board member.
Where
We are located in Zürich – a hotbed of Internet of Things activities, from research at ETH, to corporate research & development centers (e.g., IBM, Google, Microsoft, Apple) to a number of startup companies.

